Mikrotik version 7 brings many new features, including wireguard vpn. Wireguard vpn is fine, but it is layer 3 VPN – can not be bridged. What if you need L2 VPN, for example to migrate local server to datacenter and from network view keep it in your local network?
In my setup I wanted to be able migrate VMs from local Proxmox PVE to PVE running in Hetzner in datacenter. PVE in datacenter was dedicated server.
Mikrotik 7.1 also support l2tpv3, which is not very well documented in Mikrotik wiki yet, but it enables Layer 2 VPN. L2tpv3 is also supported in linux. How to create bridge between them?
Linux side:
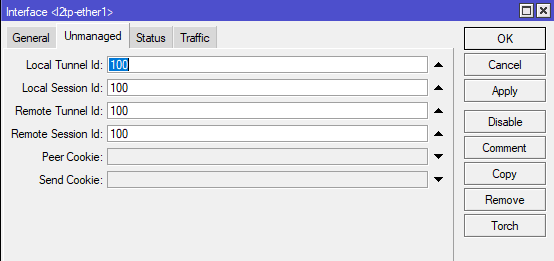
ip l2tp add tunnel tunnel_id 100 peer_tunnel_id 100 encap ip local 138.201.X.Y remote 62.197.X.Y ip l2tp add session tunnel_id 100 session_id 100 peer_session_id 100 ip link up l2tpeth0 ip link set l2tpeth0 mtu 1500
Mikrotik:
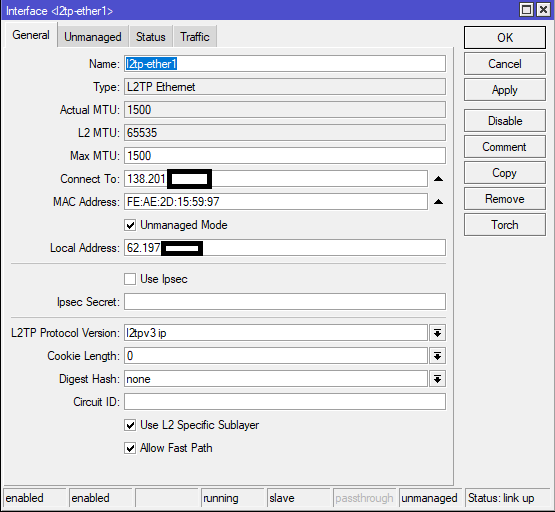
Mikrotik uses fixed port udp 1701 in UDP mode. In ip mode encapsulation ip proto 115 is used. L2 tunnel to linux must use “Unmanaged mode” and “Use L2 Specific Sublayer”. Mikrotik does not support simple IPSec mode (you can not enable “Use Ipsec”)
If you configure IP addresses on both ends of tunnel, you should be able to ping remote side. If this works, you can add interface into bridge.
bridge name bridge id STP enabled interfaces
vmbr0 8000.52283e48bab0 no fwpr102p0
fwpr200p0
l2tpeth0
Funny part – IPsec between mikrotik & linux
Since L2tpv3 is not encrypted is good idea to encrypt your traffic with ipsec. We have to use ip mode encapsulation for l2tpv3, because I did not figured out how to define policy for udp mode, which also may conflict with mikrotik l2tp server ipsec policy.
Linux side:
apt install strongswan
/etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
conn %default
keyexchange=ikev1
ikelifetime=1d
lifetime=1800s
ike=aes128-sha1-modp1024!
esp=aes128-sha1-modp1024!
# leftfirewall=yes # this is necessary when using Proxmox VE firewall rules
conn L2TP
rightprotoport=115
right=%any
leftprotoport=115
type=transport
authby=psk
auto=add
/etc/ipsec.secrets
This file holds shared secrets or RSA private keys for authentication. # RSA private key for this host, authenticating it to any other host # which knows the public part. : PSK Your_Key_Here
Mikrotik:
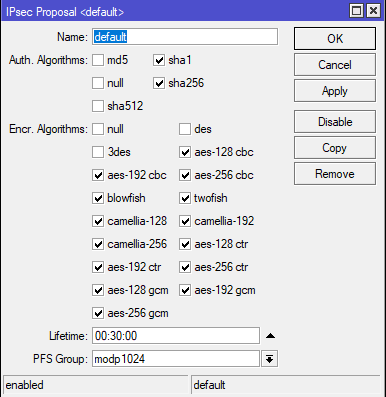
1) Default IPsec proposal:
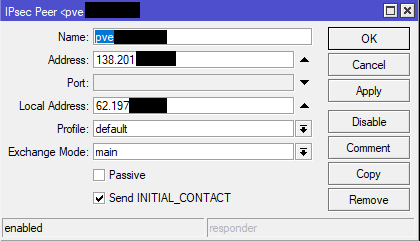
2) Add IPsec peer:
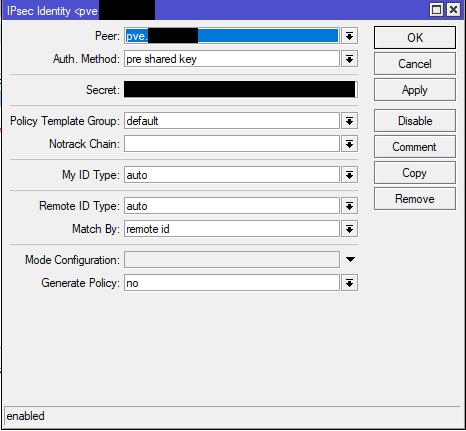
3) Add IPsec Identity with your shared key:
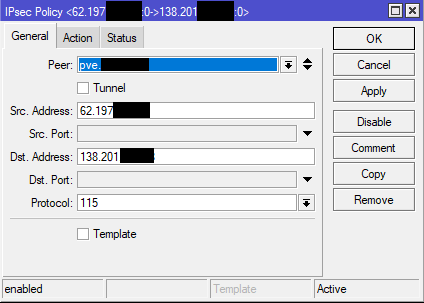
4) Define new IPsec policy:
5) Magic !
charon: 15[IKE] CHILD_SA L2TP{1077} established with SPIs c2b9f597_i 0b2e7104_o and TS 138.201.X.Y/32[l2tp] === 62.197.X.Y/32[l2tp]